Fetch CVE Data and Use Them in Your Processes
Robert Ullrich22. Aug 2018 | ConsultingCyber SecurityUse cases
Disclaimer:
The practical examples presented in our technical blog (blog.otrs.com) and now in the expert category in our FAQ blog section serve as a source of ideas and documentation to show what is theoretically possible with OTRS in concrete scenarios or sometimes even for more exotic configurations. All configurations presented here were developed under laboratory conditions as a proof of concept.
We can only guarantee testing and implementation of these concepts to be error-free and productive if implemented in a workshop with one of our OTRS consultants. Without this, the responsibility lies with the customer himself. Please note that configurations from older OTRS versions may not work in the newer ones.
As you may have noticed, OTRS Group has launched “STORM powered by OTRS” in the last year, which is used in IT security departments and companies for a long time due to the well-documented code of OTRS and a huge background in the CERT area. One of the key facts of STORM is the special consultants with a military / IT Security background for several years.
One of the features of “STORM powered by OTRS” is the information floater which was described here. To display information, this information floater is sufficient, but what will happen if you have to work with these data in a (process) ticket?
In part 1 of this small blog article series, I will show you how to request additional information for a CVE from CIRCL. I’m calling this web service CIRCLCVEConnector.
I’m using “STORM powered by OTRS” with the OTRS Feature Add-On “OTRSTicketInvoker”.
In addition, we need some dynamic fields in OTRS:
- CVENumber – Text – used to specify the CVE number
- WSCVEID – Text – the received CVE ID from CIRCL
- WSCVESummary – TextArea – a short summary which is part of every CVE
- WSCVEReferences – TextArea – references for the CVE
- WSCVEVulnerableConfigurations – TextArea – vulnerable configurations for the CVE
- WSCVSS – Text – the CVSS score of the CVE
- WSCWE – Text – Common Weakness Enumeration of the CVE
- WSCapec – Text – Common Attach Pattern Enumeration and Classification for the CVE
- WSPacketStorm – TextArea – packetstormsecurity.com reference
- WSRefmap – TextArea – some more references
- WSPublished – Text – the date when the CVE was published
- WSModified – Text – the last modification date of the CVE
- WSAllCVEInformationReceived – Text – A trigger for a later use case ;-)
Configuring the CIRCLCVEConnector in STORM
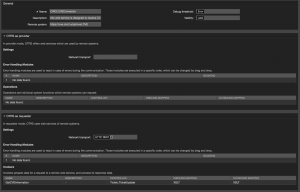
As always we need a new web service in STORM. Call it “CIRCLCVEConnector”:
A new invoker is needed:
As you can see I removed everything, except the dynamic field “CVENumber” from my outgoing request data, because I want to keep my payload small.
The next point is the XSLT mapping for our outgoing request and incoming response data:
Outgoing XSLT mapping:
Incoming XSLT mapping:
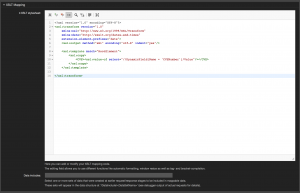
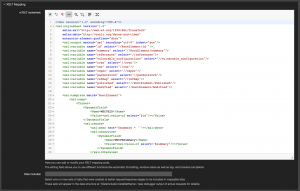 Here’s the complete XSL stylesheet:
Here’s the complete XSL stylesheet:
<?xml version="1.0" encoding="UTF-8"?> <xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform" xmlns:date="http://exslt.org/dates-and-times" extension-element-prefixes="date"> <xsl:output method="xml" encoding="utf-8" indent="yes"/> <xsl:variable name="id" select="//RootElement/id "/> <xsl:variable name="summary" select="//RootElement/summary"/> <xsl:variable name="references" select="//references"/> <xsl:variable name="vulnerable_configurations" select="//vulnerable_configuration"/> <xsl:variable name="cvss" select="//cvss"/> <xsl:variable name="cwe" select="//cwe"/> <xsl:variable name="capec" select="//capec"/> <xsl:variable name="packetstorm" select="//packetstorm"/> <xsl:variable name="refmap" select="//refmap"/> <xsl:variable name="published" select="//RootElement/Published"/> <xsl:variable name="modified" select="//RootElement/Modified"/> <xsl:template match="RootElement"> <xsl:copy> <Ticket> <DynamicField> <Name>WSCVEID</Name> <Value><xsl:value-of select="$id"/></Value> </DynamicField> <xsl:choose> <xsl:when test="$summary = ''"></xsl:when> <xsl:otherwise> <DynamicField> <Name>WSCVESummary</Name> <Value><xsl:value-of select="$summary"/></Value> </DynamicField> </xsl:otherwise> </xsl:choose> <xsl:choose> <xsl:when test="$references = ''"></xsl:when> <xsl:otherwise> <DynamicField> <Name>WSCVEReferences</Name> <Value> <xsl:for-each select="$references"> <xsl:value-of select="."/><xsl:text>
</xsl:text></xsl:for-each></Value> </DynamicField> </xsl:otherwise> </xsl:choose> <xsl:choose> <xsl:when test="$vulnerable_configurations = ''"></xsl:when> <xsl:otherwise> <DynamicField> <Name>WSCVEVulnerableConfigurations</Name> <Value> <xsl:for-each select="$vulnerable_configurations"> <xsl:value-of select="id"/><xsl:text>
</xsl:text> </xsl:for-each> </Value> </DynamicField> </xsl:otherwise> </xsl:choose> <xsl:choose> <xsl:when test="$cvss = ''"></xsl:when> <xsl:otherwise> <DynamicField> <Name>WSCVSS</Name> <Value> <xsl:value-of select="$cvss"/> </Value> </DynamicField> </xsl:otherwise> </xsl:choose> <xsl:choose> <xsl:when test="$cwe = ''"></xsl:when> <xsl:otherwise> <DynamicField> <Name>WSCWE</Name> <Value> <xsl:value-of select="$cwe"/> </Value> </DynamicField> </xsl:otherwise> </xsl:choose> <xsl:choose> <xsl:when test="$capec = ''"></xsl:when> <xsl:otherwise> <DynamicField> <Name>WSCapec</Name> <Value> <xsl:for-each select="$capec"> <xsl:value-of select="name"/><xsl:text>
</xsl:text> </xsl:for-each> </Value> </DynamicField> </xsl:otherwise> </xsl:choose> <xsl:choose> <xsl:when test="$capec = ''"></xsl:when> <xsl:otherwise> <DynamicField> <Name>WSPacketStorm</Name> <Value> <xsl:for-each select="$packetstorm"> Title: <xsl:value-of select="title"/> Source: <xsl:value-of select="data_source"/> ID: <xsl:value-of select="id"/> Last seen: <xsl:value-of select="last_seen"/>> Published: <xsl:value-of select="published"/> Reporter: <xsl:value-of select="reporter"/> Source: <xsl:value-of select="source"/> </xsl:for-each> </Value> </DynamicField> </xsl:otherwise> </xsl:choose> <xsl:choose> <xsl:when test="$refmap = ''"></xsl:when> <xsl:otherwise> <DynamicField> <Name>WSRefmap</Name> <Value> <xsl:for-each select="refmap"> Title: <xsl:value-of select="title"/> Source: <xsl:value-of select="data_source"/> ID: <xsl:value-of select="id"/> Last seen: <xsl:value-of select="last_seen"/>> Published: <xsl:value-of select="published"/> Reporter: <xsl:value-of select="reporter"/> Source: <xsl:value-of select="source"/> </xsl:for-each> </Value> </DynamicField> </xsl:otherwise> </xsl:choose> <xsl:choose> <xsl:when test="$published = ''"></xsl:when> <xsl:otherwise> <DynamicField> <Name>WSPublished</Name> <Value> <xsl:value-of select="$published"/> </Value> </DynamicField> </xsl:otherwise> </xsl:choose> <xsl:choose> <xsl:when test="$modified = ''"></xsl:when> <xsl:otherwise> <DynamicField> <Name>WSModified</Name> <Value> <xsl:value-of select="$modified"/> </Value> </DynamicField> </xsl:otherwise> </xsl:choose> <DynamicField> <Name>WSAllCVEInformationReceived</Name> <Value>Yes</Value> </DynamicField> </Ticket> </xsl:copy> </xsl:template> </xsl:stylesheet>
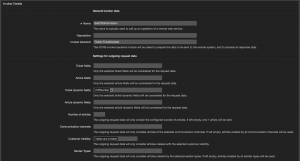
We should define the dynamic fields “WSCVEID, WSCVESummary, WSCVEReferences, WSCVEVulnerableConfigurations, WSCVSS, WSCWE, WSCapec, WSPacketStorm, WSRefmap, WSPublished, WSModified, WSAllCVEInformationReceived” as ticket dynamic fields in the web service, to store the CIRCLE CVE response. The last point for the invoker is the used event trigger. I’m using the event “TicketDynamicFieldUpdate_CVENumber”, because it makes most sense in my scenario:
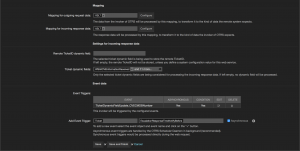
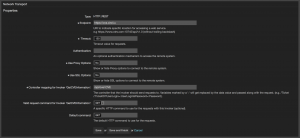
Next point is to configure the network transport. It’s an easy job:
The used endpoint is “https://cve.circl.lu“, the controller mapping “/api/cve/:CVE” and the request method is “GET”. You’ll also find this information in the https://cve.circl.lu/api/.
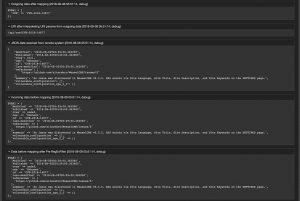
Testing the CIRCLCVEConnector
Depending on your configured event trigger for the invoker, use a valid CVE number in the dynamic field “CVENumber”. You should now see something similar in the web service debug log:
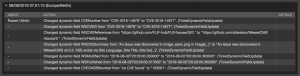
In the ticket history, we can now see that the response values are stored in the dynamic fields:
More information about the CIRCL API
Please go to the following website, if you need more information: https://cve.circl.lu/api/.