Encrypt and sign notifications in OTRS via PGP
Jens Bothe22. Aug 2017 | AdministrationConsultingUse cases
Disclaimer:
The practical examples presented in our technical blog (blog.otrs.com) and now in the expert category in our FAQ blog section serve as a source of ideas and documentation to show what is theoretically possible with OTRS in concrete scenarios or sometimes even for more exotic configurations. All configurations presented here were developed under laboratory conditions as a proof of concept.
We can only guarantee testing and implementation of these concepts to be error-free and productive if implemented in a workshop with one of our OTRS consultants. Without this, the responsibility lies with the customer himself. Please note that configurations from older OTRS versions may not work in the newer ones.
The Security Toolbox in OTRS allows to decrypt tickets in the backend and to sign and encrypt the notifications. Based on an already running PGP setup in the OTRS installation the following steps are needed:
- verify that the web server (apache) is running as OTRS user (usually otrs)
- verify that the .gnupg directory and content are owned by otrs
- verify that the public keys of the agents are stored in the keyring
- create a PGP key pair for the OTRS Notification sender (via gpg –gen-key)
Now let us start the configuration in the Sysconfig:
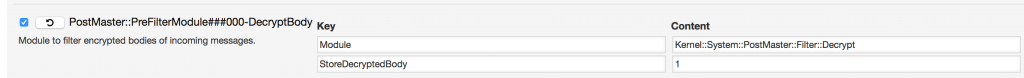
This will decrypt encrypted emails in the backend, so the content can be used to be analyzed in the Postmaster Filters or as content in the notifications. If needed you can store the decrypted body in the database which would allow full-text searches on the body.
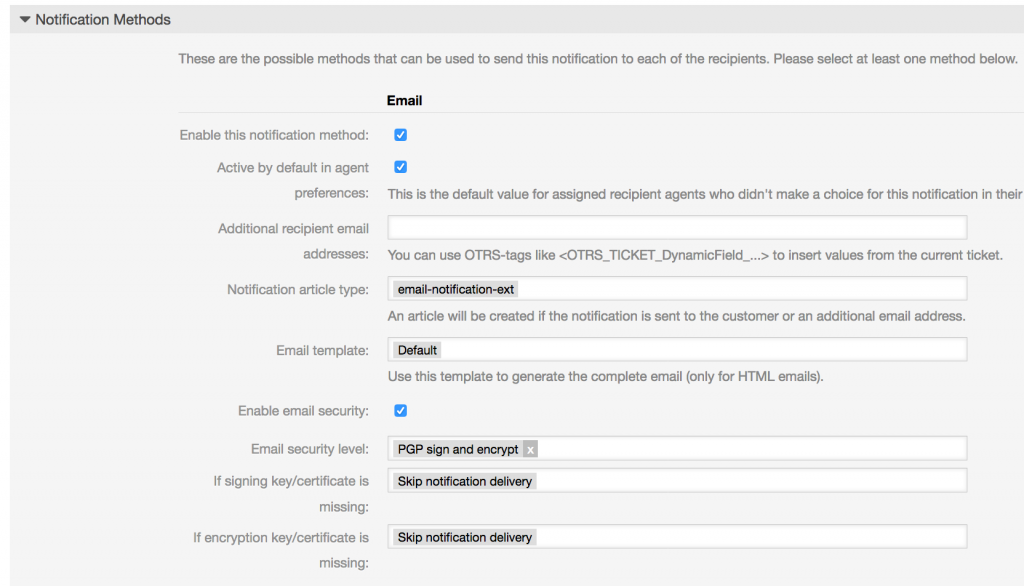
As next step, you have to alter the settings for all notifications you want to sign and/or encrypt. In my system, the encryption will be used and notifications to agents without a known key will be suppressed.
All notifications will be signed and encrypted. If the original email was encrypted it will be decrypted and newly encrypted with the keys of the agents.