Checking IP reputation via Information Floater
Jens Bothe10. Jan 2017 | AdministrationConsultingUse cases
Disclaimer:
The practical examples presented in our technical blog (blog.otrs.com) and now in the expert category in our FAQ blog section serve as a source of ideas and documentation to show what is theoretically possible with OTRS in concrete scenarios or sometimes even for more exotic configurations. All configurations presented here were developed under laboratory conditions as a proof of concept.
We can only guarantee testing and implementation of these concepts to be error-free and productive if implemented in a workshop with one of our OTRS consultants. Without this, the responsibility lies with the customer himself. Please note that configurations from older OTRS versions may not work in the newer ones.
One of the features of the OTRS 5s Security Toolbox is the information floater which allows to search for patterns in an article of a ticket. The feature was designed to enrich the content of a ticket without having to add static content to it. The main usage is to give security teams valuable information at a glance without the need to lookup the information in a separate browser tab.
Out of the box the possibility to search for CVE numbers is available via the Sysconfig settings in Ticket->Ticket::Frontend::ZoomCollectMetaFilters###CVE-Google and Ticket->Ticket::Frontend::ZoomCollectMetaFilters###CVE-Mitre. An additional use case I had to solve lately was to check whether IP addresses were listed on realtime blackhole lists (RBL).
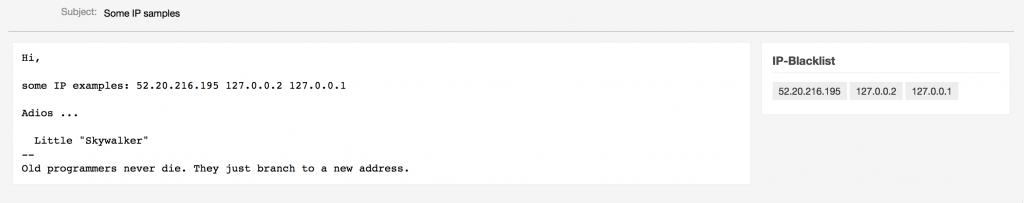
Highlighting IP addresses in the TicketZoom
So first of all I had to add an additional ZoomCollectMetaFilter which would match on IP addresses. One possible way is to extend the XML which is rendered by the Sysconfig as already described in several posts (e.g. even more RSS feeds in SysConfig). This time I directly created a perl config file “Kernel/Config/Files/ZZZIPCheck.pm” which contains the needed configuration:
$Self->{'Ticket::Frontend::ZoomCollectMetaFilters'}->{'IP-Blacklist'} = {
'Meta' => {
'Name' => 'IP-Blacklist',
'Target' => '_blank',
'URL' => 'dnsrb.pl?ip=<MATCH1>',
'URLPreview' => 'dnsrbl.pl?ip=<MATCH1>',
},
'RegExp' => [
'(\\d{1,3}\\.(\\d{1,3})\\.(\\d{1,3})\\.(\\d{1,3}))'
]
};
If an IP address is found in an article, the references will be displayed in the ticket zoom:
The Perl script
Next step is to create a perl cgi script in the bin/cgi-bin folder of the OTRS installation named dnsrbl.pl:
#!/usr/bin/perl
use strict;
use warnings;
use CGI qw(:standard);
use Net::RBLClient;
my $bl = ['ix.dnsbl.manitu.net','zen.spamhaus.org','b.barracudacentral.org','all.s5h.net','dnsbl-1.uceprotect.net','virbl.dnsbl.bit.nl','proxies.blackhole
s.easynet.nl','cbl.abuseat.org','blackholes.easynet.nl','relays.bl.kundenserver.de','agobot.bl.kundenserver.de'];
my $rbl = Net::RBLClient->new(
lists => $bl,
max_time => 5,
timeout => 1,
query_txt => 1,
max_hits => 10,
server => '8.8.8.8',
);
my $ip = param('ip');
print header(-type => 'text/html',
'X-FRAME-OPTIONS' => 'SAMEORIGIN');
print start_html(-title =>'IP Blacklist Check',
-style=>{'src'=>'//cdn.jsdelivr.net/bootstrap/3.3.7/css/bootstrap.min.css'});
print '<div class="container">';
print '<div class="well">';
print h1("Checked IP: $ip");
print '</div>';
my $result = $rbl->lookup($ip);
my @listed_by = $rbl->listed_by;
my @listed_hash = $rbl->listed_hash;
my @listed_txt = $rbl->txt_hash;
foreach my $list (keys @listed_by){
print '<div class="alert alert-danger" role="alert">';
print '<h4>';
print b($listed_by[$list],": ");
print p($listed_hash[$list]," ");
print i($listed_txt[$list]," ");
print '</h4>';
print '</div>';
}
if (! @listed_by) {
print '<div class="alert alert-success" role="alert">';
print '<h3>';
print 'IP not found on blacklist';
print '</h3>';
print '</div>';
}
print '</div>';
print end_html;
As the script uses the Net::RBLClient class, it has to be installed first. I used CPAN:
root@otrs:/opt# cpan
cpan[1]> install Net::RBLClient
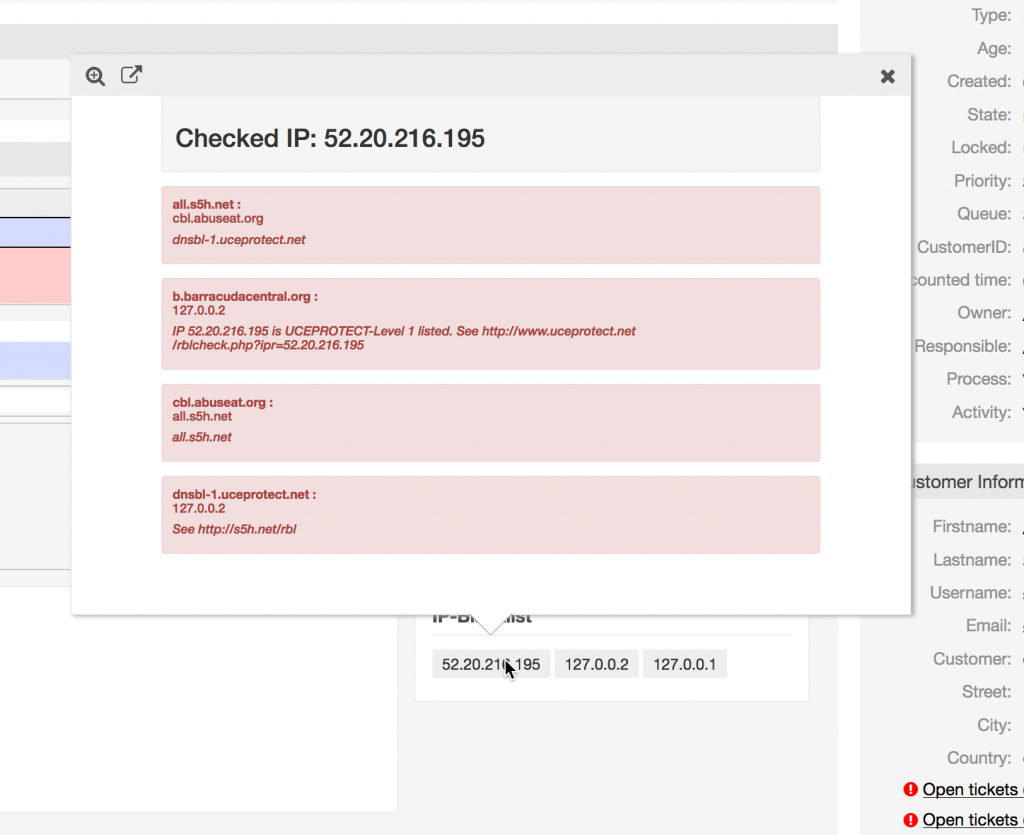
Floater Output
The floater now will lookup the ip address in the configured RBL and render the page:
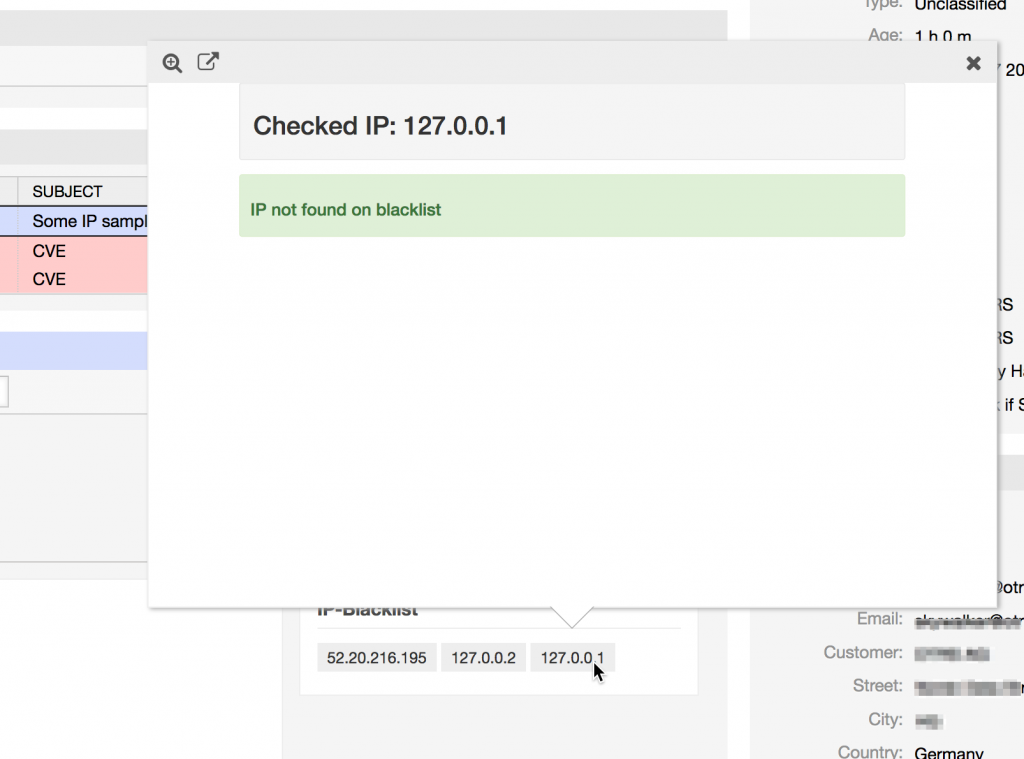
Or if no match is found:
I would really like to see your use cases and ideas to use the Information Floater of OTRS 5s, so please leave a comment.
René Kleffel at 18.07.2017, 12:41
Thank you very much. Now it works. The problem was that I only tested with "CVE-2017-058" in the article. Maybe it would be better to match it even if there are no letters before or after. My test with '.*(CVE|CAN)\\-(\\d{3,4})\\-(\\d{2,}).*' on the "CVE-2017-058" doesn't work.
Jens Bothe at 18.07.2017, 10:54
Please check ZZZAuto.pm (thats your Sysconfig settings). Easiest for testing is to switch on the CVE default (Ticket->Ticket::Frontend::ZoomCollectMetaFilters###CVE-...) Collectors and to add an article (note) to the ticket containing some Text like "Test CVE-2017-058 Test". Please also check if 3rd party add ons are installed which overwrite the TicketZoom Template
René Kleffel at 18.07.2017, 10:50
Hello Jens, I can not reproduce the function of the information floater at all. Are there any other configuration options which should be set? After Config::Rebuild the ZZZAAuto.pm shows Self->{'Ticket::Frontend::ZoomCollectMeta'} = '0'; # But it is set in SysConfig to 1 And also not any filter. the log does not show an error in debug mode. Thanks for your help.